Wizer CTF #16: Companies API
Link to challenge: CTF #16
Link to challenge: CTF #16
In this challenge, we're identifying a simple scenario of a NoSQL Injection (a.k.a. NoSQLi). Let's take a look!
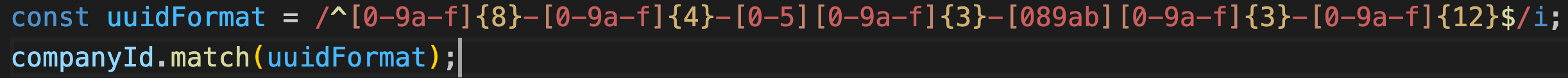
The code below introduces a simple company retrieval endpoint. The author took the time to validate that the query argument, which is a user input, does not include keywords of operators which could cause an unintended retrieval of records.
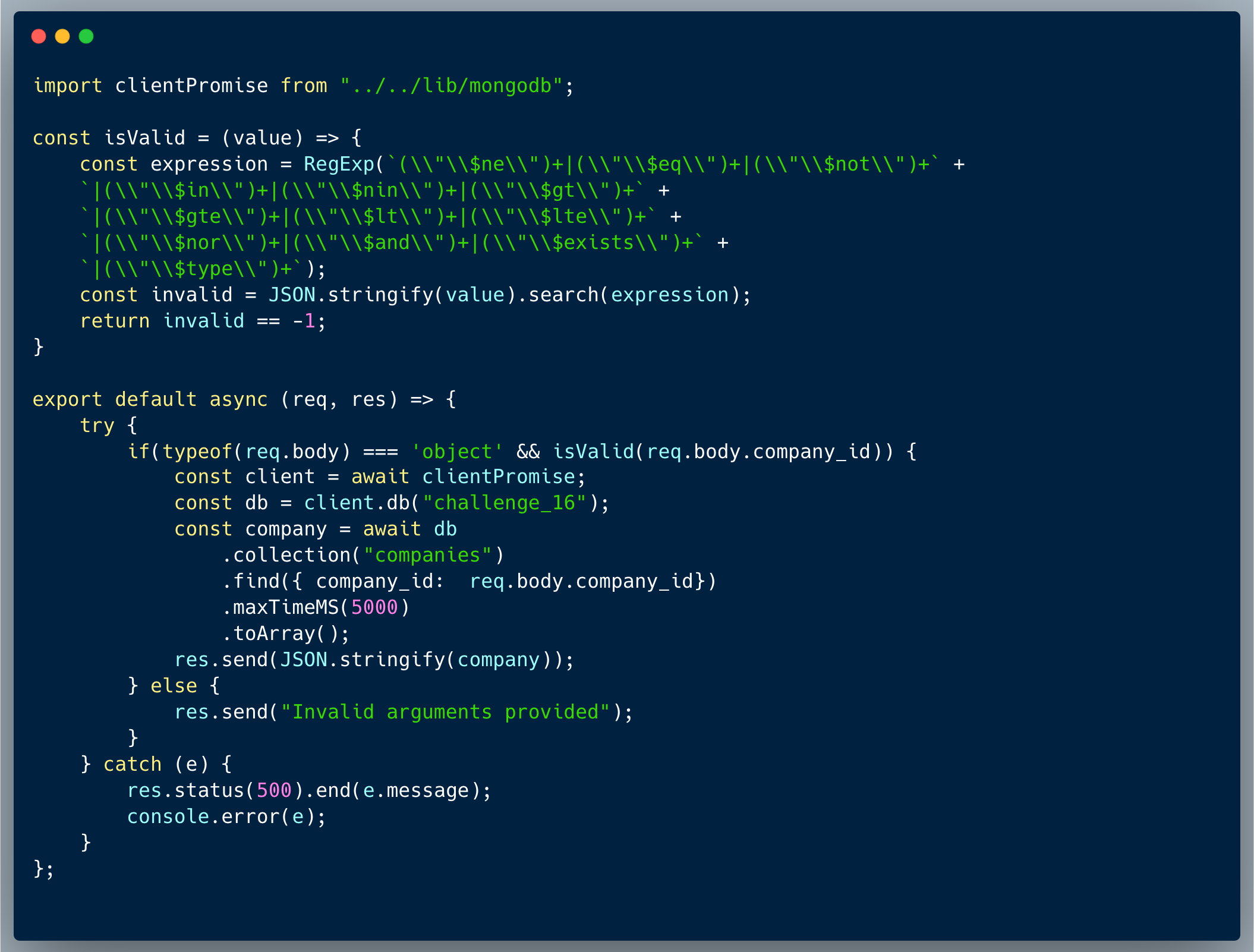
In reviewing the validation method isValid(), the author did cover almost all of the "dangerous" operators which could cause a NoSQLi. However, there's one operator that slipped and could still be used which is the $regex operator, and it's powerful enough to provide the requested outcome and cause a NoSQLi.
This is a simple case of bypass which is caused by missing a crack even-though the developer was apparently aware of the risk. The $regex could be used to generalize the query and fetch all the companies at once, overriding the intended behavior. A typical override could look like { "$regex": "[\\s\\S]*" }, a nested operator provided as the `company_id` value.
NoSQLi is a little less commonly known by developers. It is not less risky than its older brother SQLi (a.k.a. SQL Injection). The risks attached with a NoSQLi vulnerability, start with unauthorized access to data, but could get to gaining full control over a system, connecting as super-admin etc.