Wizer CTF #18: Registration and Login
Link to challenge: CTF #18
Link to challenge: CTF #18
In this challenge, we're identifying a JWT Token exploit caused by insecure secret management.
The code below showcases the typical registration, login and profile parts of an app. It is using a JWT token to send the session details back and forth between the browser and the server. The token has a signature, with means that the server can verify the integrity of the session data using that signature. The profile endpoint determines whether the user is an admin or a simple user based on an `admin` field which is encrypted within the JWT Token.
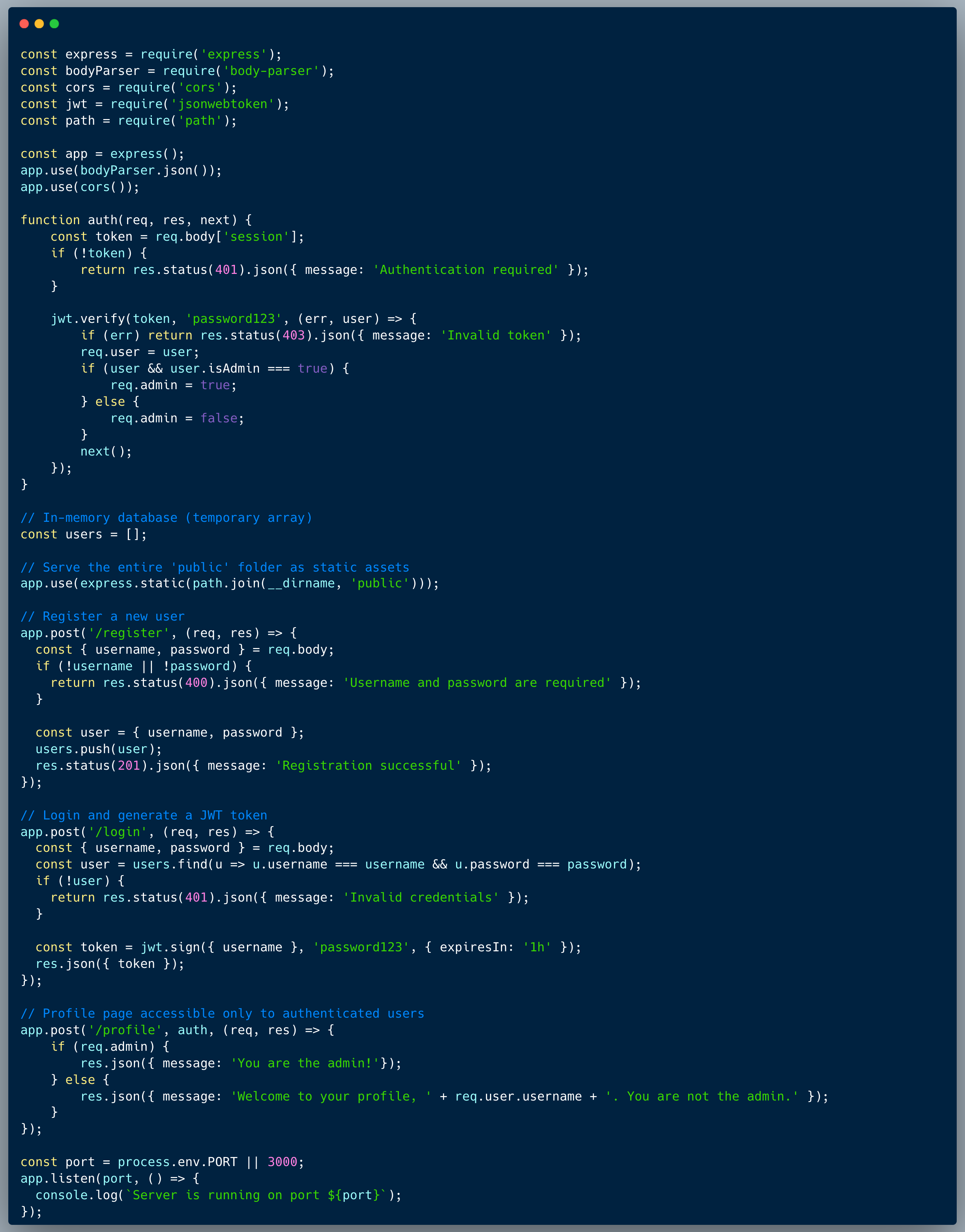
Simple: the JWT encryption password is included as clear-text within the code. Leaving keys in the code is dangerous, the developer should always assume that potential attackers could get access to it.
An attacker who gains access to the source code, could use the password to regenerate a JWT Token containing altered data. In this case, an online tool such as jwt.io could allow us to re-encrypt a token which contains the `isAdmin=true` property to trick the system into identifying
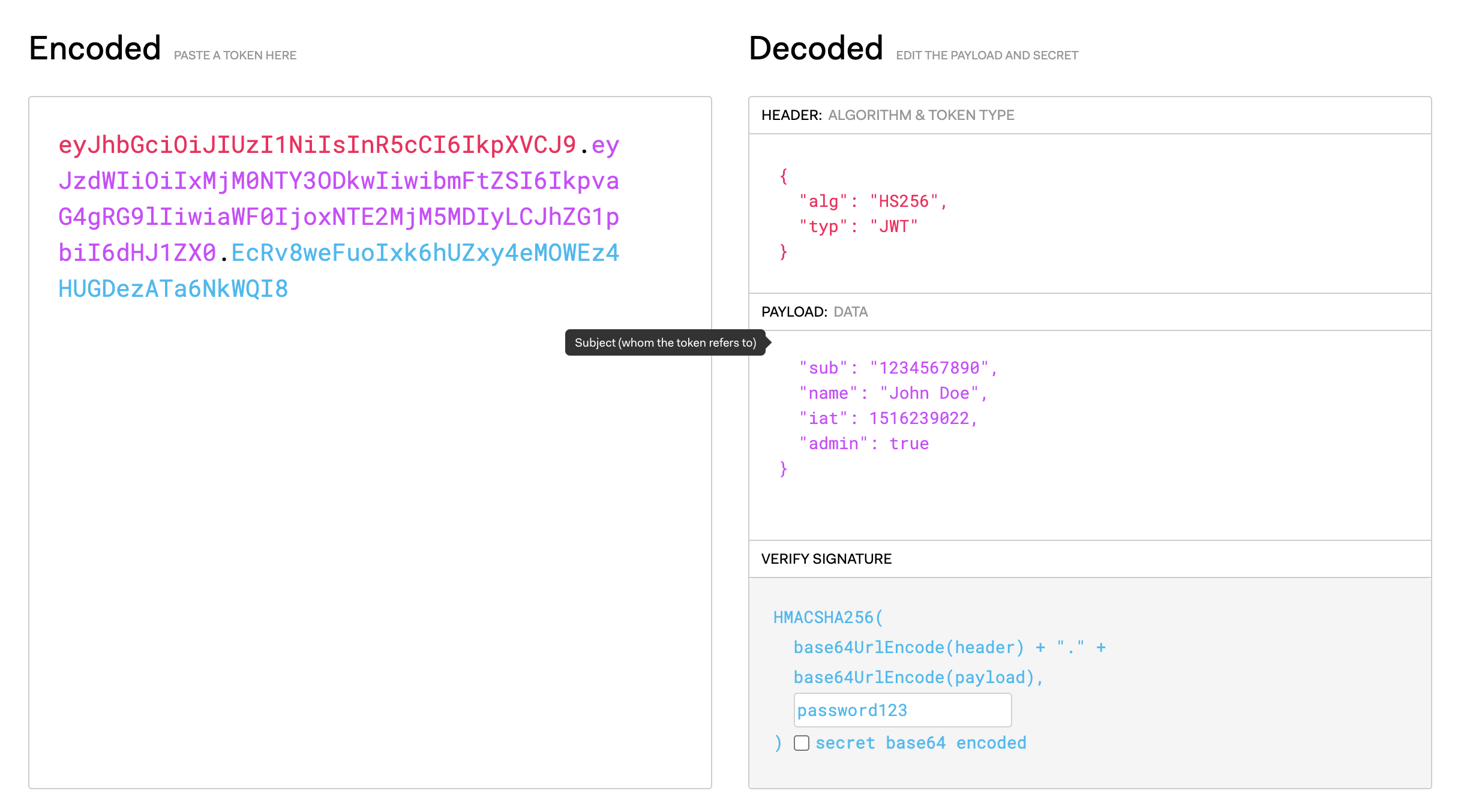
JWT Token exploits could very well mean "game-over" in terms of account take-over scenarios. Once properties which are assumed encrypted and trusted could be tempered with, the entire reason to use the best practice of a JWT Token collapses.