Wizer CTF #20: API Authentication Gateway
Link to challenge: CTF #20
Link to challenge: CTF #20
In this challenge, we're identifying a simple type of URL Parsing Confusion vulnerability.
The code below showcases an API Gateway which is responsible for authentication and relaying calls to an internal API. The internal API isn't performing authentication, since it relies on the Gateway authentication process for endpoints which are defined as `require-authentication`. The code maintains a list of endpoints which require authentication, and based on that list, it determines whether a request should be relayed to the internal endpoint after authentication or should skip it. The internal API isn't accessible externally and can be invoked via the Gateway only, for that purpose, the Gateway exposes a single endpoint named `/callApi`.
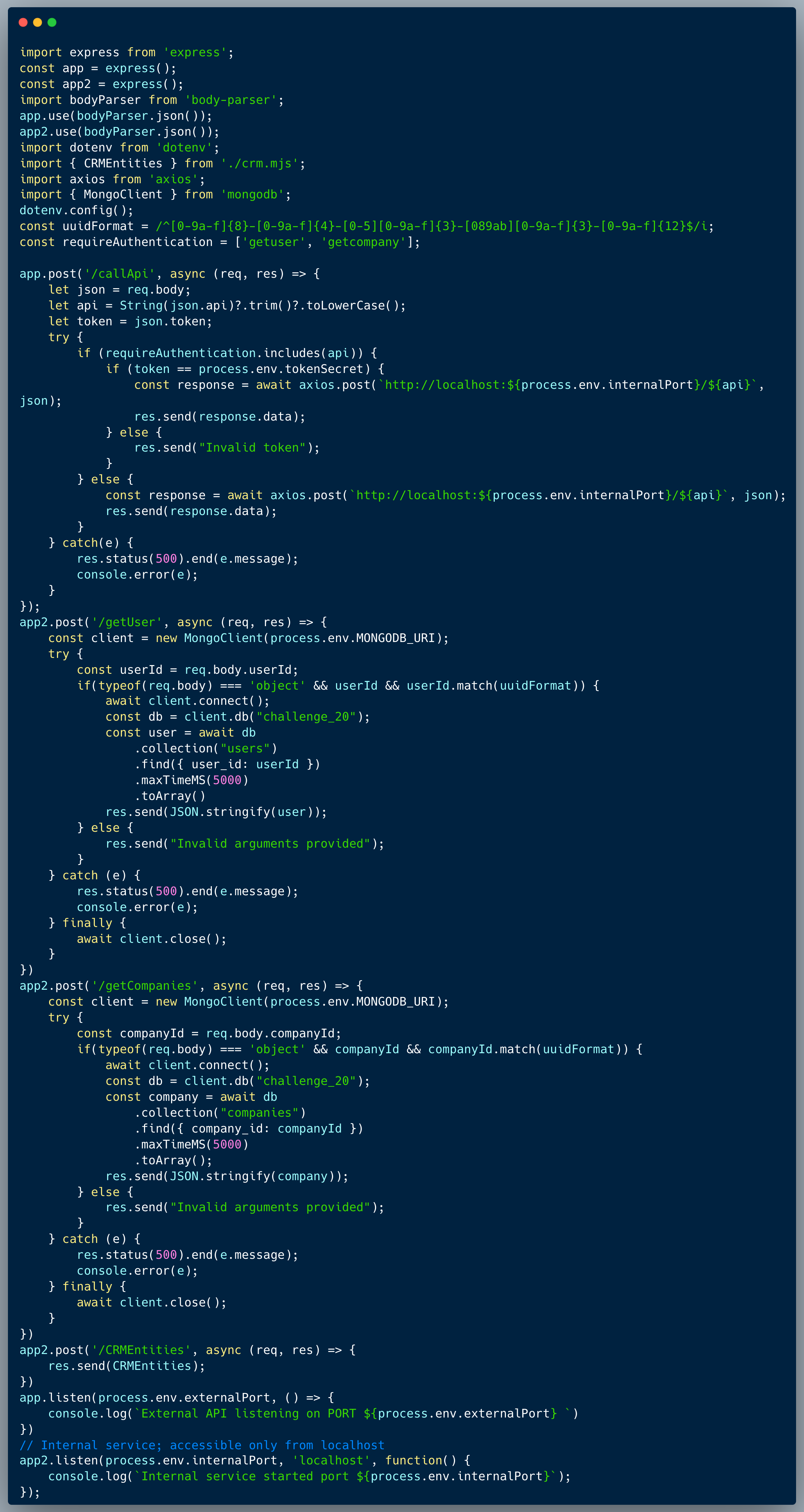
The method of validating which request needs to go through authentication isn't tight enough and a potential attacker could trick the system and bypass the authentication for endpoints which actually require it.
An attacker could identify a bypass which returns false for the `if` condition below, but is still a valid endpoint name that could successfully invoke the API within the `else` part of the condition (the `else' part is responsible to relay the call skipping authentication).
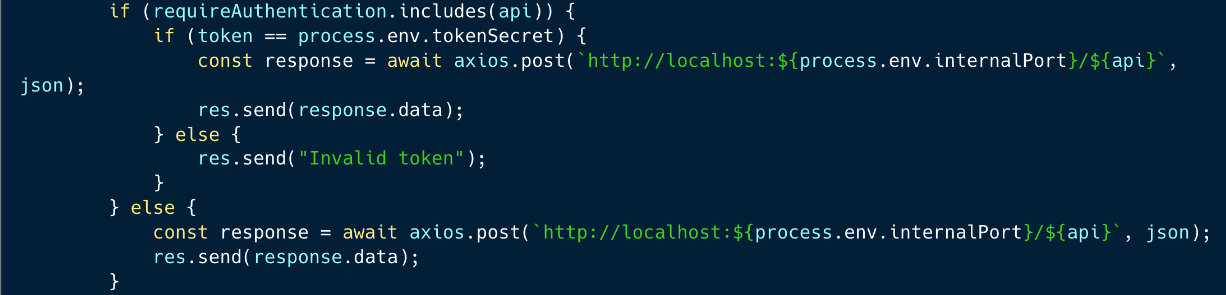
For instance, such a bypass would be adding a `/` at the end of the endpoint name, which would be considered as a different endpoint name, but still valid for the internal API.
URL Parsing Confusion exists in the wild! ...and whether it is there to support a transition process from an old system to a new system or an attempt to implement proper separation of concerns, it isn't always tightly implemented and tested. The consequences of such a vulnerability could be as severe as complete takeover when API endpoints' logic could be skipped or bypassed.