Wizer CTF #21: Menu Details
Link to challenge: CTF #21
Link to challenge: CTF #21
In this challenge, we're identifying an XSS (Cross-site Scripting) vulnerability enabled by a DOM Clobbering (window variable shadowing).
The code below demonstrates a simple app menu that integrates values from a URL, matched according to field name. The url arguments are fetched and iterated though. For every key in the querystring, if it finds an element where the id matches the key name then it embeds the value as innerText. In case it doesn't find the element, for non-debug mode, it purifies the key and prints a message that the key isn't found, however, when window.debugMode = true, both the key and value are printed without sanitization.
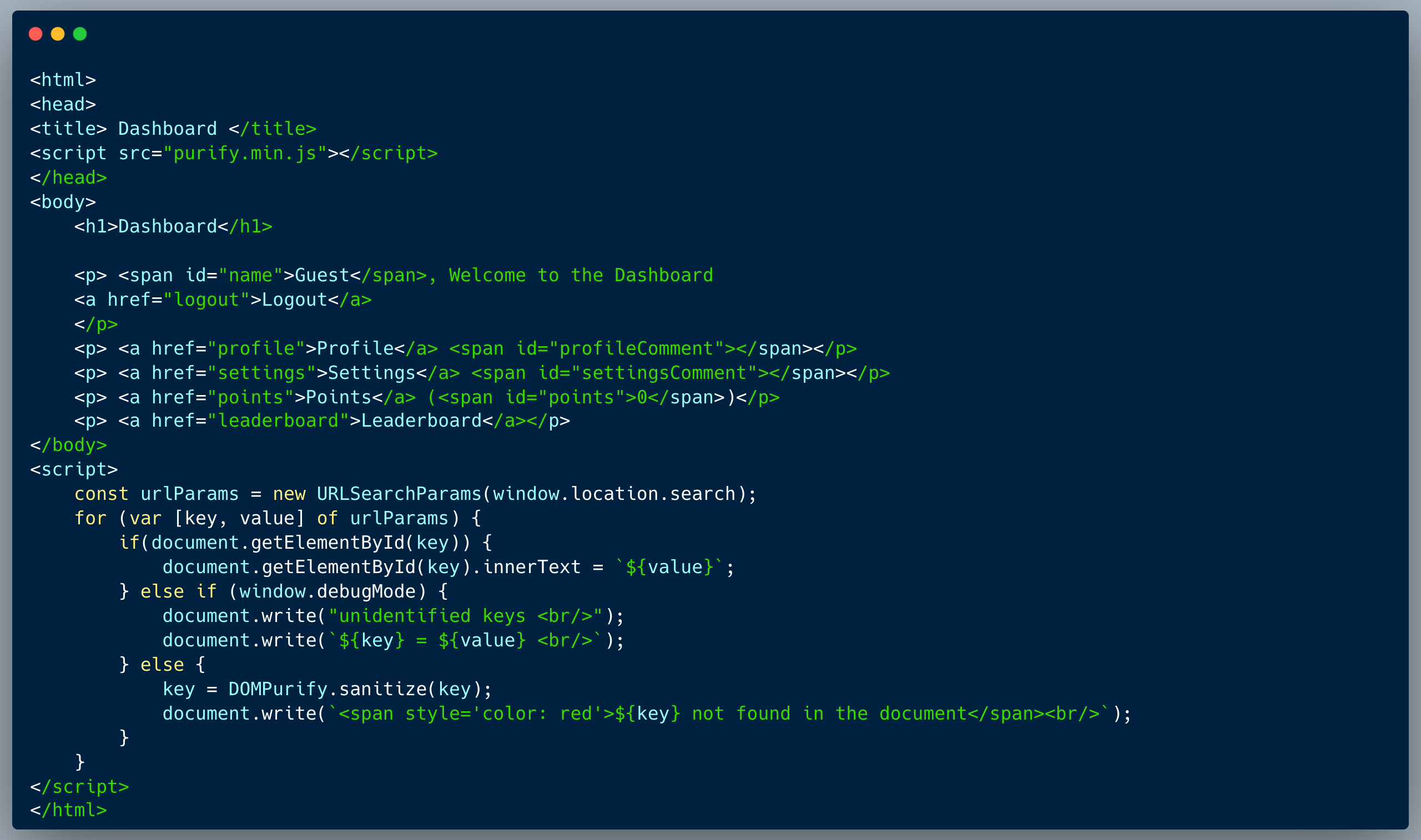
There are three issues with the code: (1) it enables debugMode using a global window argument which could be potentially shadowed by DOM Clobbering techniques, and (2) debugMode skips sanitization upon printing key/value, hence assuming you can activate this mode, you're able to print out HTML code including malicious scripts, and (3) An HTML injection is present when not in debug mode (Root cause of the DOM clobbering)
An attacker who identifies the vulnerability, could still print a valid HTML element by providing an argument which doesn't have a matching field. If that element is a `div` with an id="debugMode", then window.debugMode is effectively shadowed and the following condition is met:

To achieve XSS, the next argument provided on the querystring could include a script tag and cause an alert. The querystring of the payload could look like:
?<div-element-with-debud-mode-id>&non-existing-field=<malicious-script>
While the code injection required to capture the flag is absolutely harmless, once an XSS attack is possible, it could be immensely harmful. Once attackers are able to run Javascript within the context of a logged-in user, by using a phishing attack or other social engineering techniques, they could cause someone to click the link with the payload and execute an attack to hijack session cookies and/or perform actions on their behalf. This is just the entry point, once the attackers are in the system with any user’s credentials, they can then identify and exploit other vulnerabilities such as broken access control (a.k.a. IDOR), weak encryption / hashing and others to execute wider attacks. DOM Clobbering is a technique that could be used to bypass security controls and enable the attacker to run malicious scripts, the consequences of which could open the door for multiple types of attacks essentially changing the code flow and enabling unintended behaviors, in this case it was used to enable an XSS attack.