Wizer CTF #32: Tell me who your friends are #2
Link to challenge: CTF #32
Link to challenge: CTF #32
In this challenge, we're exploring another example of a typical IDOR vulnerability.
The code in this challenge showcases a typical players and friends/followers model. The relevant endpoints are: `/player` which runs a simple select query to fetch a player record by ID from the database, and `/friends` which selects the friends of a specific player by ID.
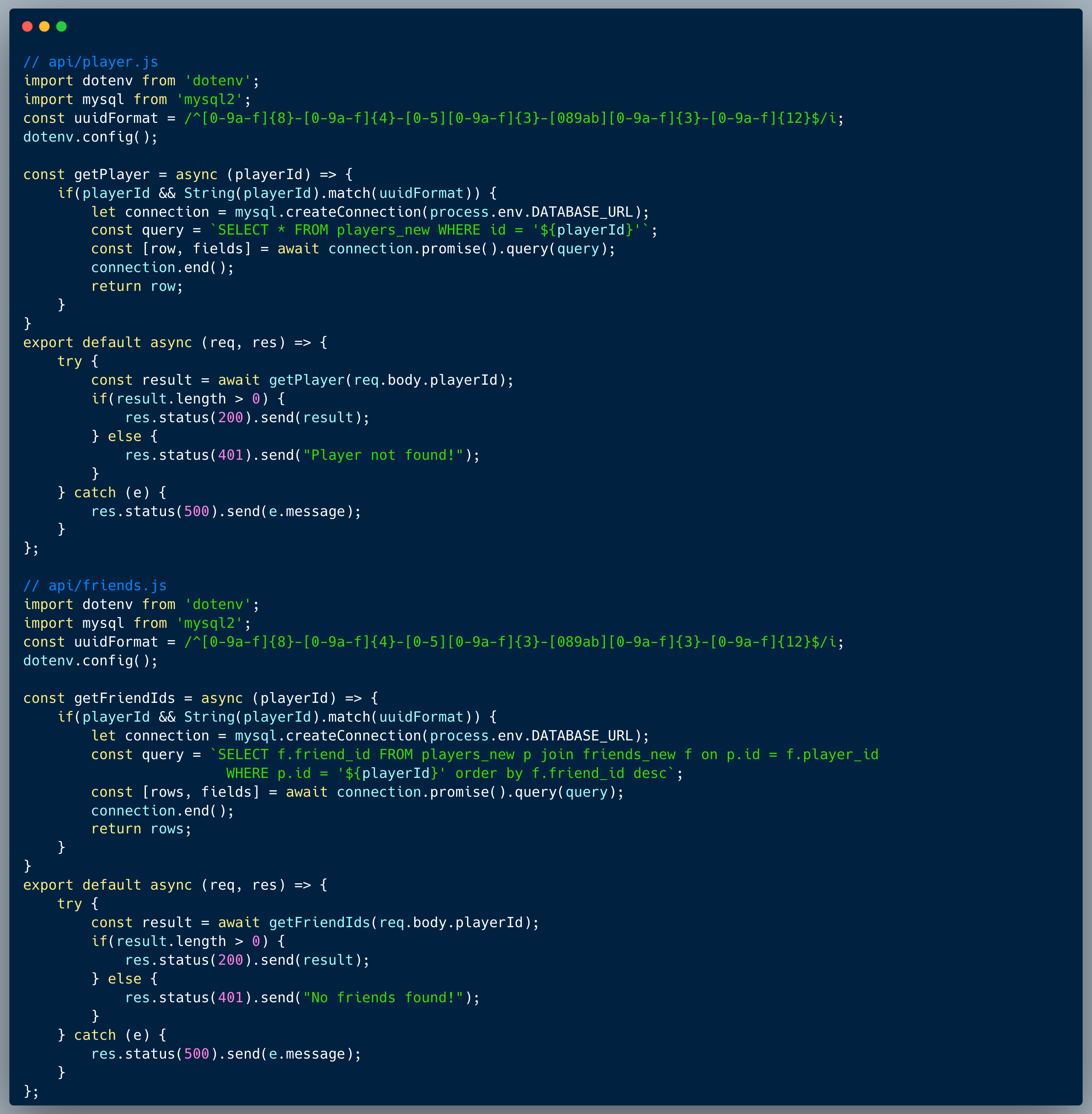
The issue with this approach is that the `/friends` endpoint does not validate the user making the request. This means that any user can request the friends of any other user by simply changing the ID in the request. This is a classic example of Insecure Direct Object Reference (IDOR) vulnerability, where an attacker can access data that they should not have permission to access. The only question here is how do we find the ID of the specific player that the challenge is asking us to get?
A successful IDOR attack would involve an attacker changing the ID in the request to the ID of the target player. For example, if the attacker knows the ID of the player they want to target, they can simply make a request to `/friends?playerId=<target_player_id>` and retrieve the friends of that player, that's the IDOR. To get the ID of the player we want to target, we can start scanning down the tree of friends, first `James Robins` direct friends, then each of their friend's friends etc. In this case, within two hops from `James Robins` account, you will find the target player `Lee Wung`.
This vulnerability poses a serious risk as it allows attackers to access sensitive information about other users without their consent. In this case, the damage might seem limited, since there's not much information in the data it stores. However in the wild, an attacker could potentially gather information about a target player's friends, which could either be sensitive, or used for social engineering attacks or other malicious purposes. Scammers often use Personally Identifiable Information (PII) to build trust and mislead their victims, hence PII is considered sensitive information which is explicitly examined for compliance purposes.